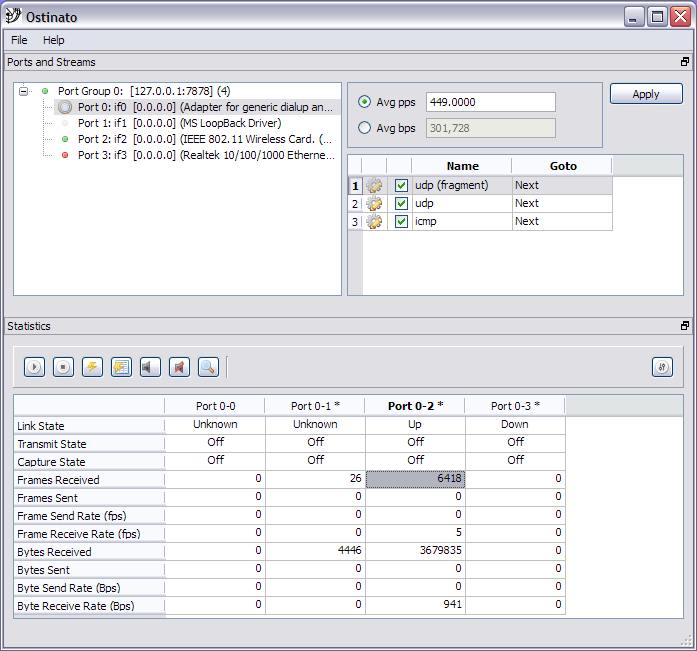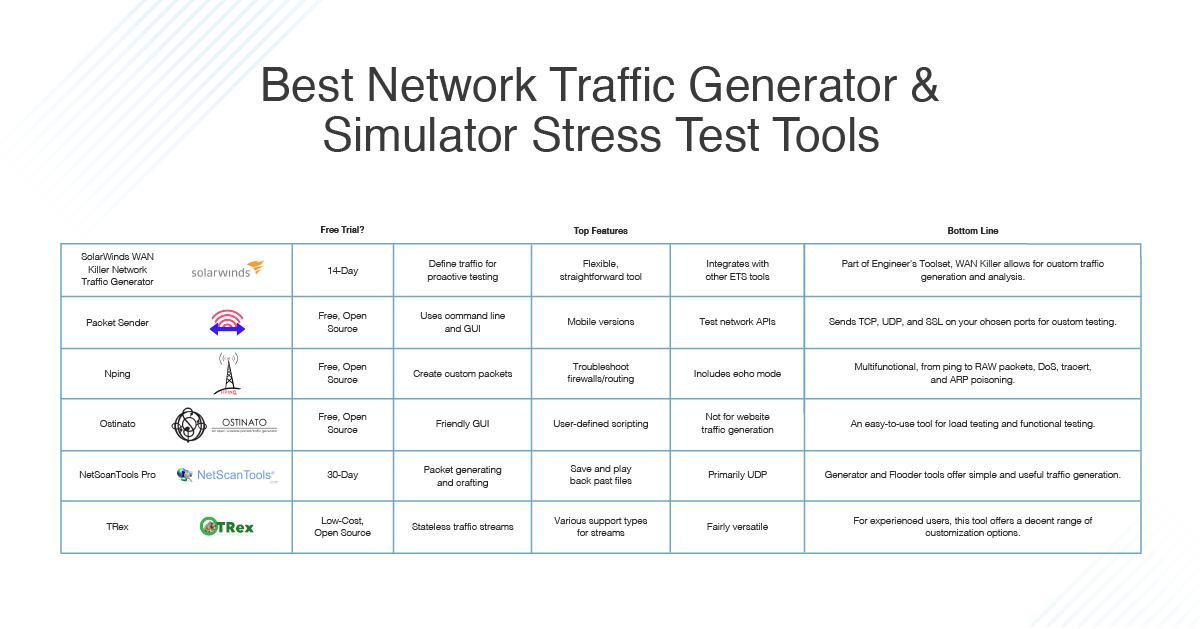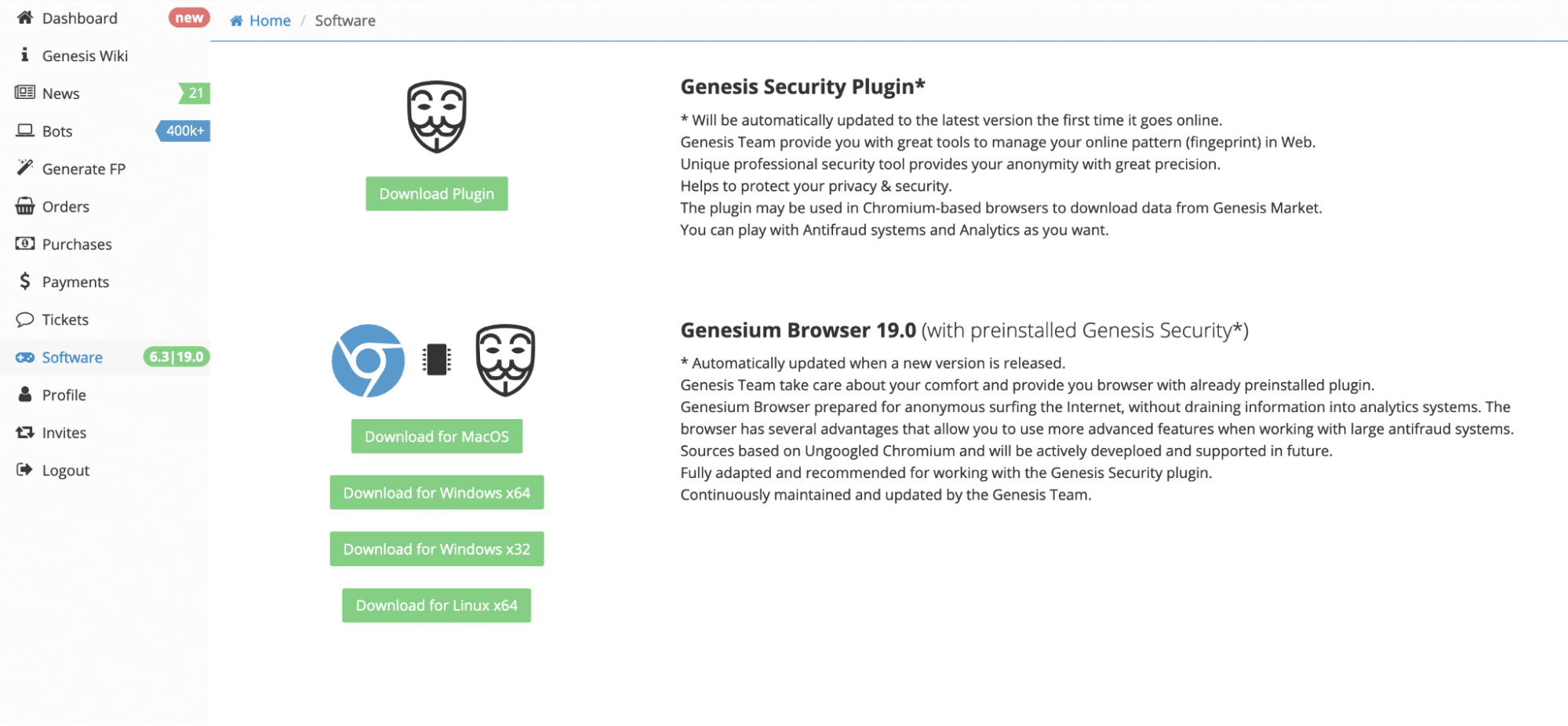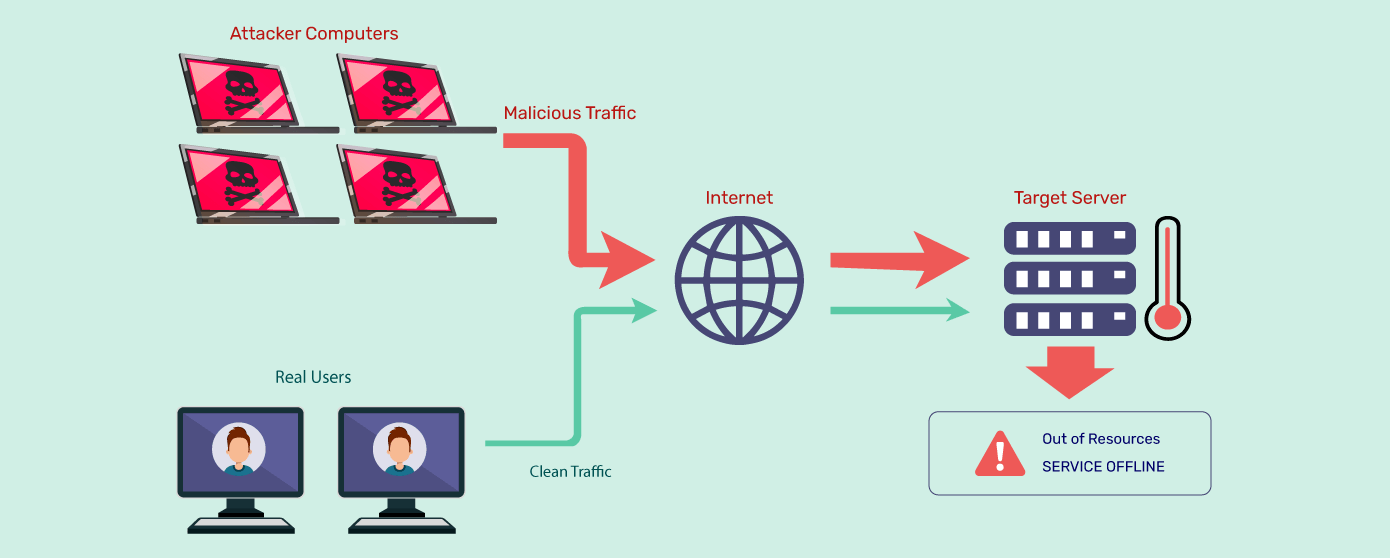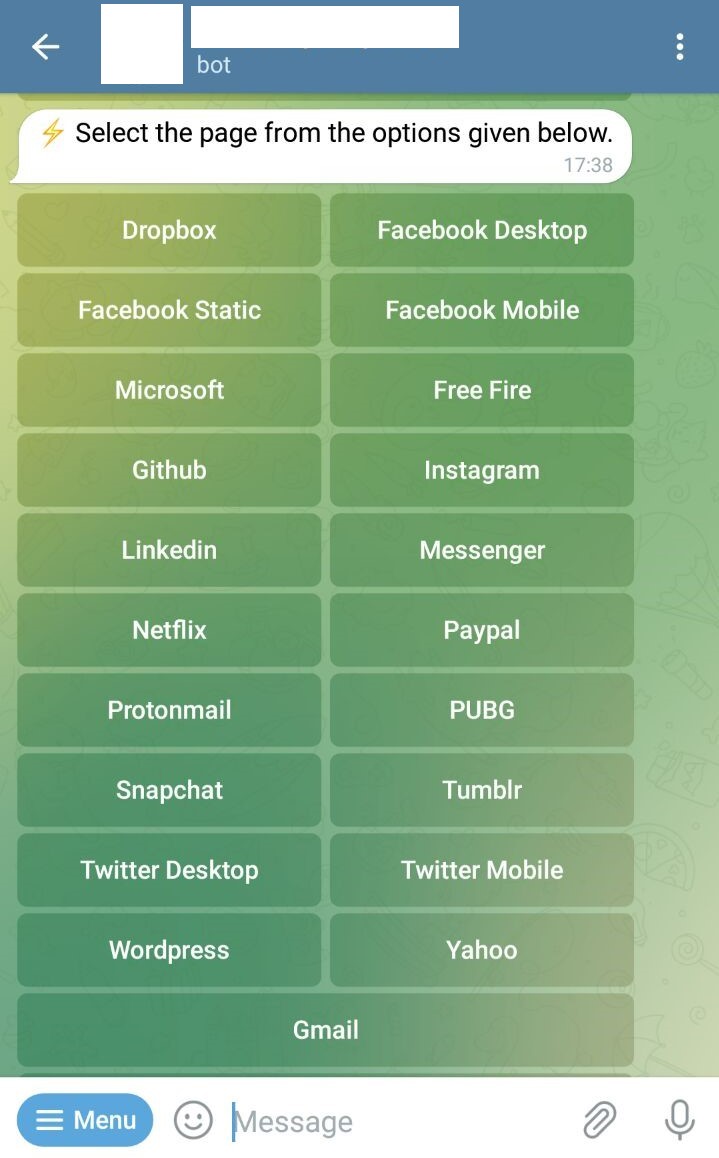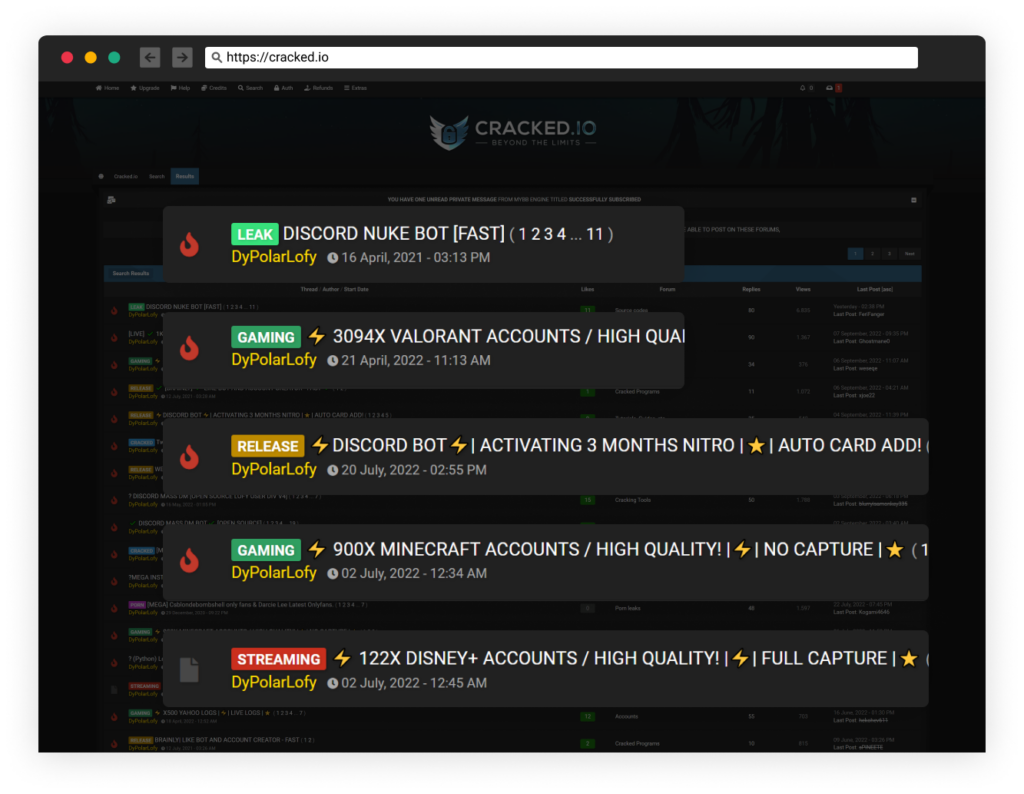
LofyGang - Software Supply Chain Attackers; Organized, Persistent, and Operating for Over a Year | Checkmarx.com

Anomaly based network intrusion detection for IoT attacks using deep learning technique - ScienceDirect

Sensors | Free Full-Text | SGAN-IDS: Self-Attention-Based Generative Adversarial Network against Intrusion Detection Systems
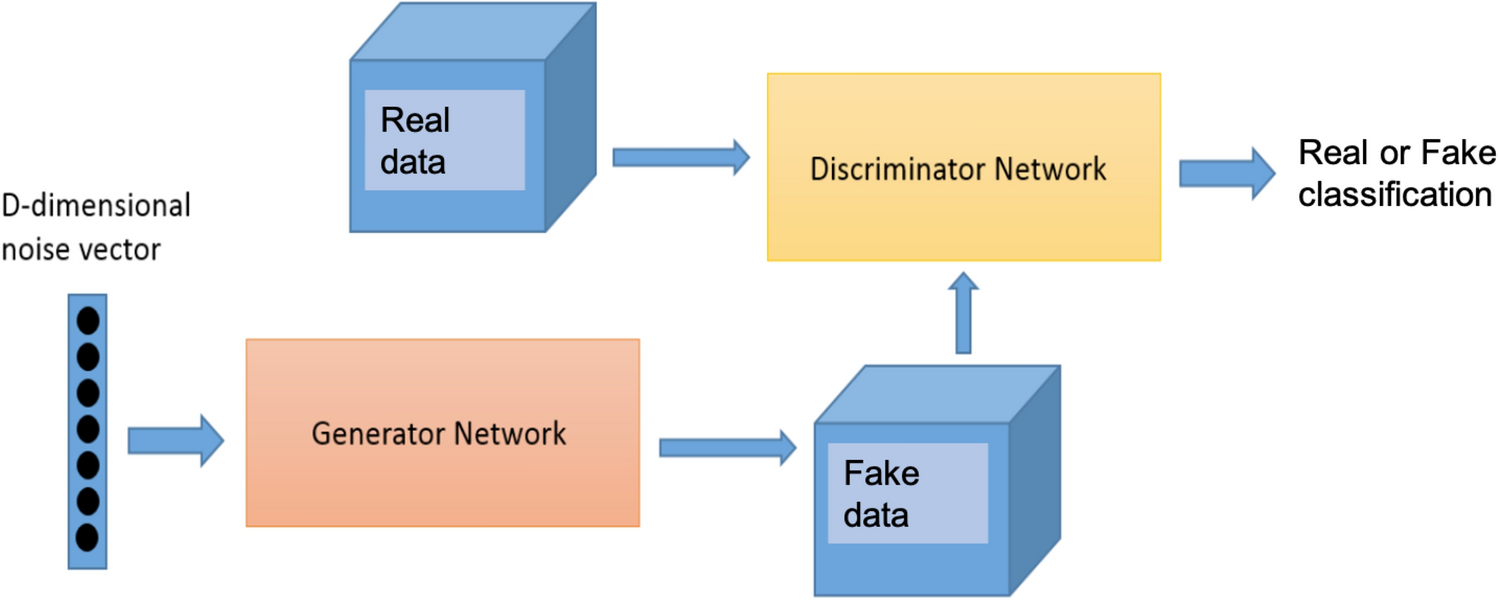
Synthetic flow-based cryptomining attack generation through Generative Adversarial Networks | Scientific Reports
Facebook Flooded with Ads and Pages for Fake ChatGPT, Google Bard and other AI services, Tricking Users into downloading Malware - Check Point Blog